Description
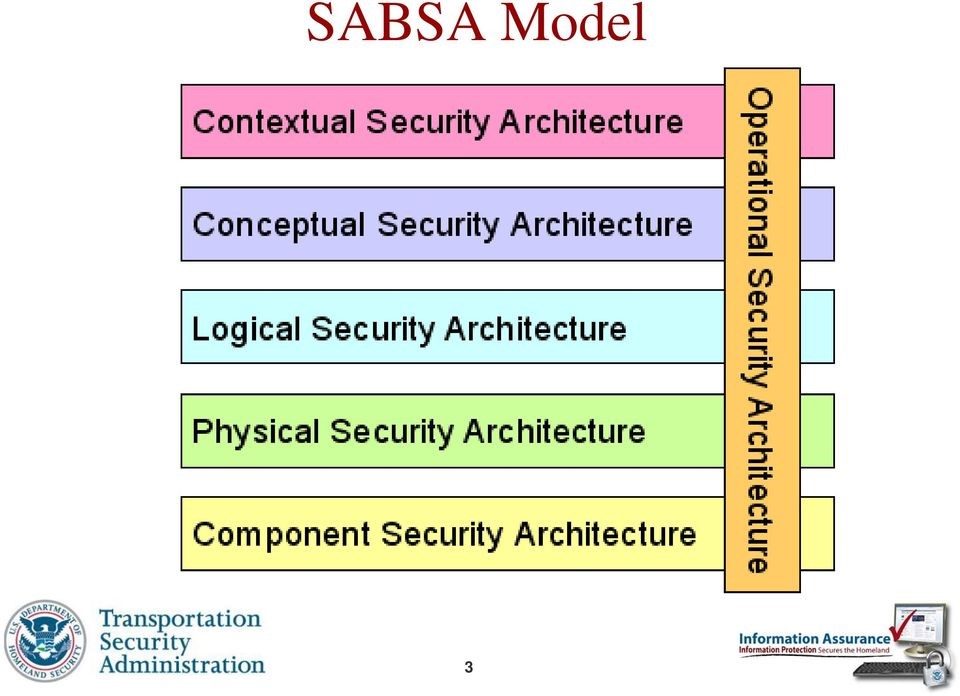 |
|
Cybersecurity Technologies & Market – Focus on Europe – 2017-2022
|
Cyber-attacks against European targets are becoming increasingly more frequent and more sophisticated, pushing existing security capabilities to the limit. New solutions and the rapid expansion of networks and services indicate that this information overload will only worsen.
Considering the economic and business implications of cyber-attacks, it has now become mandatory for the Europeans to significantly increase their investments in state-of-the-art cybersecurity technologies, solutions and outsourced services to detect, prevent, analyze, and resolve the epidemics of cyber-crime and cyber-terror.
The Cyber Security report presents:
A. Market data – analyzed via 2 independent key perspectives:
With a highly-fragmented market, we address the “money trail” (each dollar spent is analyzed and crosschecked via 2 orthogonal viewpoints):
- 18 national markets:
- UK
- France
- Netherlands
- Belgium
- Sweden
- Norway
- Finland
- Denmark
- Germany
- Austria
- Switzerland
- Italy
- Spain
- Poland
- Hungary
- Czech Republic
- Russia
- Rest of Europe
- 3 Revenue source markets:
- Products sales
- Aftersales revenues (maintenance & upgrades)
- Other revenues (consulting, planning, training, contracted services and government funded R&D)
B. European cybersecurity market analysis:
- Business opportunities and challenges
- Cybersecurity market SWOT analysis
- Market dynamics
- Market drivers and inhibitors
C. Dozens of European cybersecurity legislation and standards
D. Current & emerging technologies & services, key facts, sector background and analysis of the following 15 cybersecurity sectors:
2. Identity and Access Management
3. Mobile Enterprise Management
4. Mobile Security
5. Security Information and Event Management (SIEM)
6. Content Security
7. Malware Mitigation
8. Data Loss Prevention (DLP)
9. Datacenter Security
10. Firewalls
11. Next Generation Firewalls
12. IDS/IPS
13. Unified Threat Management (UTM)
14. Cloud-Based Services
15. Vulnerability/Risk Management & Managed Security Services
E. Vendors Data on 190 cybersecurity companies operating in the market (profiles, contact information & management personnel):
41st Parameter, Accenture, Agiliance, AhnLab, Airbus, AirWatch, Akamai, Alert Logic, AlertEnterprise, AlienVault, Alt-N Technologies, Application Security, AppSense Limited, Arbor Networks, Attachmate, Authentify, AVAST Software, Aveksa, AVG Technologies, Avira, Barracuda Networks, Beyond Security, BeyondTrust, Bit9, Bitdefender, BlackBerry, BlackStratus, Blue Coat Systems, BoxTone, Bromium, BullGuard, Cassidian Communications Inc., Catbird Networks, Centrify, Cenzic, Check Point, CipherCloud, Cisco Systems Inc, Clearswift, Click Security, CloudFlare, CloudLock, Code Green Networks, Commtouch Software, Comodo, CORE Security, Corero Network Security, Courion, Covisint, CrowdStrike Holdings, CSID, Cyber Operations, Cyber-Ark, CyberArk Software, Cyberoam, Cyren, Damballa, DigiCert, Digital Info Security Company, EdgeWave, EiQ Networks, Elbit Systems, Enterasys Networks, Entrust, ESET, Exobox Technologies Corp, Extreme Networks, Faronics Technologies, Fast facts, Fiberlink, Fidelis Security Systems, FireEye, FireMon, ForeScout Technologies, FoxGuard Solutions, F-Secure, Fulcrum IT Services Company. LLC, G2 Web Services, Gemalto, General Dynamics, GFI Software, Good Technology, Guardian Analytics, Guidance Software, Hewlett-Packard Co, HyTrust, ID Analytics, Igloo Security Inc, Imprivata, Intel Security Group, International Business Machines Corp, Intrusion Inc, IOActive, Iovation, Juniper Network, Kaspersky Lab, L-3 Communications, Lacoon Security Ltd, Lancope, LANDesk Software, LogRhythm, Lookingglass Cyber Solutions, Lookout Mobile, Lumension Security, M5 Network Security, Mandiant, Mantech International Corp, Memento, Merlin International, MessageLabs, MetricStream, Mobile Active Defense, Mobile Vault, MobileIron, Mobilityone Ltd, Mocana, MU Dynamics, N-Dimension Solutions, NetCentrics Corporation, Network Security Systems, Nics Tech Co. Ltd., NIKSUN, NSS Labs Inc., Odyssey Technologies, Okta, OpenDNS, Palantir Technologies Inc, Palo Alto Networks Inc, Panda Security, ParetoLogic, Perimeter Internetworking Corp., PerspecSys, Ping Identity, Prolexic Technologies, Proofpoint, Qualys Inc., Quick Heal Technologies (P) Ltd., QUMAS, QuoVadis, Radware Ltd, Rapid7, Raytheon Pikewerks Corporation, Red Lambda Inc., ReD plc, RedSeal Networks Inc., Retail Decisions Plc, RLM Communications Inc., RSA Security LLC, SafeNet Inc., SailPoint Technologies Inc., SAINT Corporation, Salient Federal Solutions Inc., SecurityMetrics, Senetas Corp Ltd, SilverSky, Skybox Security Inc., SolarWinds, Solera Networks Inc., Sophos Ltd., Sotera Defense Solutions Inc., Splunk Inc., Stormshield Network Security (Formerly: NETASQ S.A.), Strikeforce Technologies, Symantec Corporation, Sympli ied Inc., Synectics Plc, Tangoe, TeleSign Corp., Tenable Network Security, Thales, The KEYW Holding Corporation, ThreatMetrix, TIBCO Software, TraceSecurity, Trend Micro Inc, Tripwire, Trusteer, Trustwave, Utimaco Safeware Inc., Vanguard Integrity Professionals Inc., Varonis Systems, VASCO Data Security International, Venafi, Veracode, Verdasys, Verint Systems Inc, WatchGuard Technologies, Webroot, WhiteHat Security, Workshare Technology, Zix Corporation, Zscaler
The Cyber Defense Market report includes the following appendices:
Appendix B: The European Union Challenges and Outlook
Appendix C: Europe Migration Crisis & Border Security
Appendix D: Abbreviations
This Cybersecurity Technologies & Market – Focus on Europe – 2017-2022 report is a valuable resource for executives with interests in the industry. It has been explicitly customized for industry and decision-makers to identify business opportunities, emerging technologies, market trends and risks, as well as to benchmark business plans.
Questions answered in this 386-page report include:
- What will the European Cybersecurity market size be in 2017-2022?
- Where and what are the Cybersecurity market opportunities?
- What are the Cybersecurity market drivers and inhibitors?
- What are the challenges to the Cybersecurity market?
The Cybersecurity Technologies & Market – Focus on Europe – 2017-2022 report presents in 386 pages, 24 tables and 32 figures, analysis of current situation in this market. This report, granulated into 36 national and revenue source submarkets, provides for each submarket 2015-2016 data and assessments, and 2017-2022 forecasts and analyses.




















