Description
 |
|
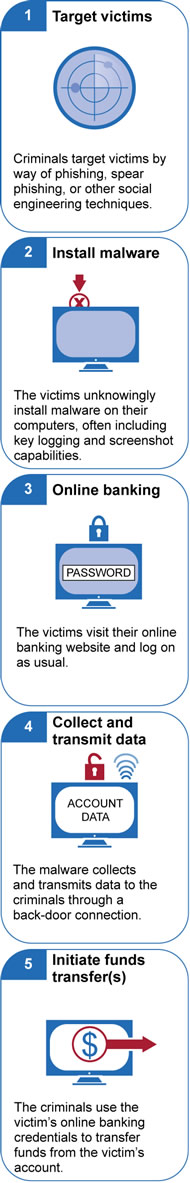
Steps Involved in Financial Account Takeovers Source: U.S. Congress GAO July 2015 |
This cyber security market report focuses on the U.S. financial services demand side of cyber security products, systems & services. It is based on hundreds of interviews with financial institutions’ cyber security customers, CEOs, CISOs and CIOs as well as cyber security industry executives and world-class experts.
The surge and sophistication of “successful” cyber crimes against the U.S. financial services enterprises, major retail chains, and banks during 2013-2015, when over 600 million customers’ bank records and payment cards were compromised, shook the board rooms of the U.S. financial institutions.
Considering the economic and business implications of cyber attacks, it has now become mandatory for the financial industry to significantly increase its investments in state-of-the-art cyber security technologies, solutions, and outsourced services to detect, prevent, analyze and resolve the epidemic of financial cyber crime.
According to the Cyber Security Market Report “U.S. Financial Services: U.S. Financial Services: Cybersecurity Systems & Services Market – 2016-2020” report, the U.S. financial institutions cyber security market is the largest and fastest growing private sector cyber security market. Its cumulative 2016-2020 market size is forecasted to exceed $68 Billion.
We corroborated our findings by conducting a meta study which integrated the results of eight individual surveys performed by others (e.g., Verizon, IBM, SANS survey for: Blue Coat, FireEye, ForeScout, Raytheon, Sourcefire Tenable Network, N.Y. State Department of Financial Services, Accenture, Zurich Insurance and more) with thousands of combined responders.
This report is a resource for executives with interests in the cyber security industry. It has been explicitly customized for the cyber security industry and financial services decision-makers to identify business opportunities, developing technologies, market trends and risks, as well as to benchmark business plans.
Questions answered in this 663-page report include:
- What will the market size and trends of the cyber security market for financial institutions be during 2016-2020?
- Which are the submarkets that provide attractive business opportunities in this cyber security segment?
- What is the U.S. financial institutions industry structure?
- Who are the decision-makers?
- What drives the U.S. banking & financial services managers to purchase cyber security solutions and services?
- What are the customers looking for?
- What are the technology & services trends?
- Where and what are the market opportunities?
- What are the market drivers and inhibitors?
- Who are the key cyber security vendors?
- What are the challenges to market penetration & growth?
The report examines each dollar spent in the market via two orthogonal money trails: Technology & Service sectors and the Financial Services sectors that procure the products & services. Within these trails, the report is further granulated into: 25 technologies, solutions & services and 12 financial industry sectors as shown below:
|
|
Also included with this report: a roster of 21,653 banking and financial services enterprises that are potential cyber security customers. 87% of the listed enterprises include corporate contact information. Provided in an Excel file, the roster is segmented into 10 U.S. financial industry sectors (Banks, Credit Card Issuers, Credit Unions, Insurance Companies, Pension Funds, Accounting Companies, Stock Brokerage Companies, Stock Exchanges, Mortgage Companies and Real Estate Investment Companies).
We particularly look into the retail industry primes and the payment cards industry commitment to replace the 1970s security technology magnetic stripe cards and point of sale cash card scanners by new chip & pin cards and POS reading equipment.
The report presents in 663 pages, 259 tables & figures, analysis of 23 current and pipeline cyber security services & technologies and 193 leading cyber security vendors. It is explicitly tailored for both the cyber security industry and banking & financial services industry decision-makers. The report details market & cyber security legislation trends, and enables the two communities to identify business opportunities, present pipeline technologies, cyber security market size, legislation trends, drivers and inhibitors. It also provides for each submarket 2013 -2014 data, analyses, and projects the 2015-2020 market and technologies from several perspectives, including:
- Business opportunities and challenges
- SWOT analysis
- Market analysis (e.g., market dynamics, market drivers and inhibitors)
- 2013-2020 market size data & forecasts, current & emerging technologies & services, key facts, sector background and analysis of the following 18 submarkets:
1. Endpoint Security
2. Identity and Access Management
3. Mobile Enterprise Management
4. Mobile Security
5. Security Information and Event Management
6. Content Security
7. Data Loss Prevention (DLP)
8. Datacenter Security
9. Firewall
10. Next Generation Firewall
11. IDS/IPS
12. Unified Threat Management
13. Cloud-Based Services
14. Vulnerability/Risk Management & Managed Security Services
15. Consulting Services
16. Integration Services
17. Education and Training Services
18. Forensics, VPN, Web Security, Policy & Compliance and Other Services - 2013-2020 market size data & forecasts, key facts and analysis of 7 banking & financial services sectors:
1. U.S. Banking Industry
2. U.S. Insurance Industry
3. U.S. Credit Card Companies & Mobile Payment Providers industry
4. U.S. Government Related Financial Services industry
5. U.S. Stock Brokerages & Exchanges
6. U.S. Pension Funds industry
7. U.S. Credit Unions, Investment Funds, Accountancy Companies & Other financial sectors
The report includes:
- 8 Appendices:
Appendix A: Other Banking & Financial Services Cybersecurity Solutions
Appendix B: Techno-Tactical Trends
Appendix C: Cyberspace Layers
Appendix D: Cybersecurity Standards
Appendix E: The E.U. Banking and Financial Services Security Regulations
Appendix F: Payment Card Transactions & Security Systems
Appendix G: Financial Sector Acronyms & Glossary
Appendix H: NIST – Framework for Improving Critical Infrastructure Cybersecurity
- Data on 191 Cybersecurity companies operating in the market (profiles, contact information & management personnel) including:
41st Parameter, Accenture, Agiliance, AhnLab, Airbus, AirWatch, Akamai, Alert Logic, AlertEnterprise, AlienVault, Alt-N Technologies, Application Security, AppSense Limited, Arbor Networks, Attachmate, Authentify, AVAST Software, Aveksa, AVG Technologies, Avira, Barracuda Networks, Beyond Security, BeyondTrust, Bit9, Bitdefender, BlackBerry, BlackStratus, Blue Coat Systems, BoxTone, Bromium, BullGuard, Cassidian Communications Inc., Catbird Networks, Centrify, Cenzic, Check Point, CipherCloud, Cisco Systems Inc, Clearswift, Click Security, CloudFlare, CloudLock, Code Green Networks, Commtouch Software, Comodo, CORE Security, Corero Network Security, Courion, Covisint, CrowdStrike Holdings, CSID, Cyber Operations, Cyber-Ark, CyberArk Software, Cyberoam, Cyren, Damballa, DigiCert, Digital Info Security Company, EdgeWave, EiQ Networks, Elbit Systems, Enterasys Networks, Entrust, ESET, Exobox Technologies Corp, Extreme Networks, Faronics Technologies, Fast facts, Fiberlink, Fidelis Security Systems, FireEye, FireMon, ForeScout Technologies, FoxGuard Solutions, F-Secure, Fulcrum IT Services Company. LLC, G2 Web Services, Gemalto, General Dynamics, GFI Software, Good Technology, Guardian Analytics, Guidance Software, Hewlett-Packard Co, HyTrust, ID Analytics, Igloo Security Inc, Imprivata, Intel Security Group, International Business Machines Corp, Intrusion Inc, IOActive, Iovation, Juniper Network, Kaspersky Lab, L-3 Communications, Lacoon Security Ltd, Lancope, LANDesk Software, LogRhythm, Lookingglass Cyber Solutions, Lookout Mobile, Lumension Security, M5 Network Security, Mandiant, Mantech International Corp, Memento, Merlin International, MessageLabs, MetricStream, Mobile Active Defense, Mobile Vault, MobileIron, Mobilityone Ltd, Mocana, MU Dynamics, N-Dimension Solutions, NetCentrics Corporation, Network Security Systems, Nics Tech Co. Ltd., NIKSUN, NSS Labs Inc., Odyssey Technologies, Okta, OpenDNS, Palantir Technologies Inc, Palo Alto Networks Inc, Panda Security, ParetoLogic, Perimeter Internetworking Corp., PerspecSys, Ping Identity, Prolexic Technologies, Proofpoint, Qualys Inc., Quick Heal Technologies (P) Ltd., QUMAS, QuoVadis, Radware Ltd, Rapid7, Raytheon Pikewerks Corporation, Red Lambda Inc., ReD plc, RedSeal Networks Inc., Retail Decisions Plc, RLM Communications Inc., RSA Security LLC, SafeNet Inc., SailPoint Technologies Inc., SAINT Corporation, Salient Federal Solutions Inc., SecurityMetrics, Senetas Corp Ltd, SilverSky, Skybox Security Inc., SolarWinds, Solera Networks Inc., Sophos Ltd., Sotera Defense Solutions Inc., Splunk Inc., Stormshield Network Security (Formerly: NETASQ S.A.), Strikeforce Technologies, Symantec Corporation, Sympli ied Inc., Synectics Plc, Tangoe, TeleSign Corp., Tenable Network Security, Thales, The KEYW Holding Corporation, ThreatMetrix, TIBCO Software, TraceSecurity, Trend Micro Inc, Tripwire, Trusteer, Trustwave, Utimaco Safeware Inc., Vanguard Integrity Professionals Inc., Varonis Systems, VASCO Data Security International, Venafi, Veracode, Verdasys, Verint Systems Inc, WatchGuard Technologies, Webroot, WhiteHat Security, Workshare Technology, Zix Corporation, Zscaler
- Contact Info of 87% of the following U.S. Financial Institutions (in an attached Excel file):
Financial Sector # of Firms Banks 6665 Credit Card Issuers 770 Credit Unions 6977 Insurance Companies 944 Pension Funds 252 Accounting Companies 1277 Stock Brokerage Companies 3817 Stock Exchanges 18 Mortgage Companies 831 Real Estate Investment Companies 92 Total 21,643
For more research on Cyber Security see in our Big Data Market in HLS in our site
























